As businesses push more data and applications into the cloud and the workforce demands more flexibility and remote working options, IT and security professionals are tasked with keeping the increasingly complicated infrastructure connected and secure from both outside and inside threats. A key step in this journey is implementing a centralized solution for users, applications, data, networks, and devices regardless of where they reside.
Palo Alto Networks commissioned Forrester Consulting to conduct an objective Total Economic Impact™ (TEI) study and examine the potential return on investment (ROI) enterprises realize when deploying Palo Alto Networks for network security SD-WAN.The purpose of this study is to provide readers with a framework to evaluate the potential financial impact of Palo Alto Networks’ products on their organizations. These products include next-generation firewalls (NGFWs), Cloud-Delivered Security Services including internet-of-things (IoT) security, and Prisma software-defined wide-area network (SD-WAN).
Palo Alto Networks network security and SD-WAN solutions help organizations centralize management, maintain optimum connectivity, and extend security policies and controls to every user, application, and device.
For a short description of the Palo Alto Networks solutions discussed in this study, please refer to the Product Glossary after the final page of the report.
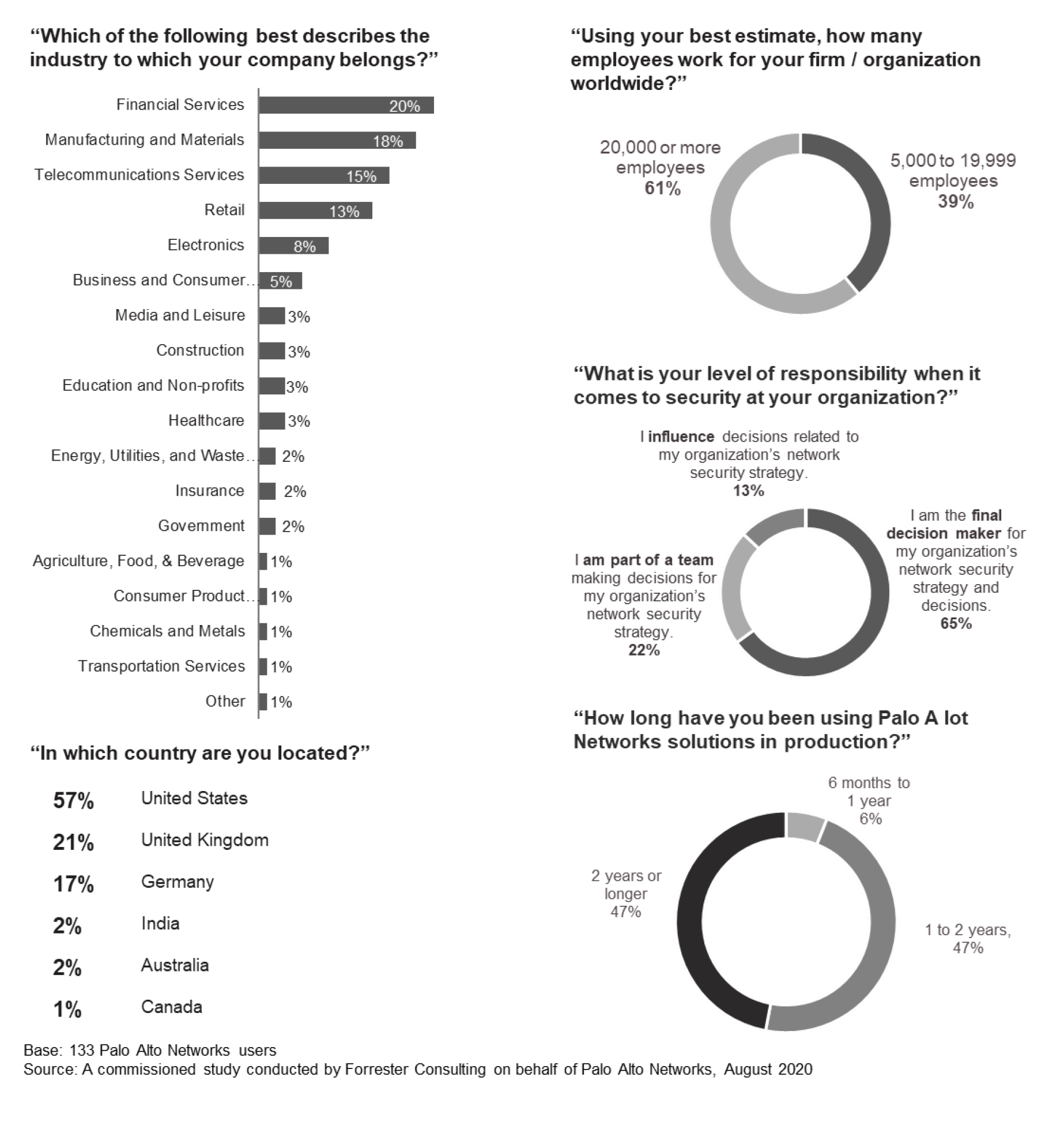
To better understand the benefits, costs, and risks associated with this investment, Forrester interviewed nine customers and surveyed 133 customers with experience using Palo Alto Networks solutions. For the purposes of this study, Forrester aggregated the experiences of the interviewed and surveyed customers and combined the results into a single composite organization.
Prior to deploying Palo Alto Networks for network security needs, the customers leveraged traditional firewalls with point solutions to secure their environments. This was a byproduct of digital transformation efforts. The organizations lacked modern security technology as security and IT teams tried to keep up with evolving business needs. Digital transformation initiatives pushed more data, applications, and processes to the cloud while other core business functions remained on-premises. Adding to the complexity was the need for the organizations to support more flexible and remote work options for their employees as employee expectations and other environmental factors drove up demand for remote access to critical applications and data. This piecemeal approach left organizations with as many as 17 different vendors in their security stacks, and made it challenging for security operations (SecOps) teams to integrate technologies, benefit from analytics, apply consistent policies, and deliver a consistent experience to end users.
Additionally, the lack of a unified platform and next-generation firewall capabilities left the organizations stuck in a cycle of devoting valuable resources to management, operations, and maintenance activities while work on new initiatives and enhancements fell to the wayside.
After the investment in the Palo Alto Networks network security solution, the customers had a common platform that fed into a centralized tool: Palo Alto Networks’ security management solution, Panorama. This significantly reduced investigational effort and freed up valuable resources to focus on enhancements and securing more of the network. The interviewees’ organizations deployed some or all of these network security and SD-WAN solutions from Palo Alto Networks.
Key results from the investment are highlighted by: efficiency gains for IT, security, and networks operations teams, business end users, and in-store workers; a reduced likelihood of a data breach with the enablement of Zero Trust; reduced costs associated with licensing and managing legacy point-solution infrastructure; and improvements to both IoT Security and SD-WAN capabilities.
- Nicholas Ferrif,
- Henry Huang,
- Japser Narvil
Project Contributors:
Key Statistics
-
Return on investment (ROI)
247%
-
Net present value (NPV)
$28.5M
Key Financial Findings
-
ROI
247%
-
Benefits PV
$40.1M
-
NPV
$28.5M
-
Payback
6 months
Quantified projected benefits. Risk-adjusted present value (PV) quantified benefits include:
-
Reduced number of security incidents requiring manual investigation by 35%, decreased mean-time-to-resolution (MTTR) by 20%, and reduced number of end point devices requiring reimaging, all resulting in $5.1 million saved over three years.
Deploying Palo Alto Networks security solutions significantly improved visibility into the organizations’ networks and introduced automation capabilities that drove down the number of critical alerts, including false positives, over time. Additionally, the organizations were able to reduce MTTR because analysts now had the data they needed at their fingertips. As a result, there were fewer malware infections and other issues with end point devices, reducing the workload for the IT operations team.
-
Improved end-user productivity with fewer incidents and investigations, totaling $865,226 over three years.
With Palo Alto Networks security solutions, end users spend less time interacting with the security and IT operations teams, and they spend more time focusing on their primary roles and driving value for their organizations.
-
Decreased likelihood of a data breach by 45% after three years.
With Palo Alto Networks, the organizations were able to enact a Zero Trust security model and apply consistent security policies across the entire organization. Cloud-Delivered Security Services supplemented the existing SecOps team and added 24/7 monitoring, vulnerability and threat prevention, and support.
-
Avoided and rationalized security infrastructure, saving $9.9 million over three years.
The organizations removed legacy security systems and products after deploying Palo Alto Networks. With as many as 17 vendors in their security stacks prior to investing, simplifying the environment and reducing the number of vendors was a priority, and the Palo Alto Networks solution provided superior coverage with less overhead. Some of the technologies that were supplanted by Palo Alto Networks include intrusion prevention (IPS/IDS), secure web gateway (SWG), web proxy, VPN malware analysis (e.g., sandboxing), DNS, and software-as-a-service (SaaS) application security.
-
Reallocated roughly 50% full-time security professionals to higher-value initiatives due to management efficiencies from a common platform, saving $1.9 million over three years.
Removing legacy vendors and consolidating to a common platform meant fewer people were required to perform the same tasks, allowing the organizations to reduce their management teams by roughly half. Additionally, the common platform allowed the organizations to quickly roll out updates, patches, and security policies to the entire platform from a centralized location, rather than updating each security device manually.
-
Saved $1.4 million on IoT from reduced management effort and a reduction in the number of new IoT devices purchased.
With IoT Security, the organizations were able to identify and secure all their IoT devices from a central platform, quickly understand the health and location of each device, and maximize the value and utilization of each device with the enhanced reporting capabilities. This reduced new purchases by 10%.
-
Reduced time to achieve proper security posture by 30%, saving $812,860 over three years.
By leveraging Palo Alto Networks’ NGFWs and Cloud-Delivered Security Services, the organizations were able to stand up their security solutions faster and reach steady state more quickly. This gave the security teams a head start on optimizing the solution to the Zero Trust standards compared to using point solutions.
-
Cut costs on WAN hardware and connectivity at remote sites by over 90%, representing $6.04 million over three years.
By migrating away from multiprotocol label switching (MPLS) to Palo Alto Networks Prisma SD-WAN, the organizations were able to significantly reduce monthly operating costs at their sites while improving visibility and control of network traffic.
-
Reduced management effort by half for IT teams and improved efficiency of branch office and retail store workers by 12% with Prisma SD-WAN, saving $4.9 million over three years.
With an intuitive UI and purpose-built hardware, Prisma SD-WAN enabled centralized management of the SD-WAN for IT teams. Additionally, the improved bandwidth, network performance, and security controls allowed the organizations to deploy better technology to their remote workers, improving productivity and customer experience.
Unquantified benefits. Benefits that are not quantified for this study include:
-
Using fewer vendors and systems allowed security professionals to invest in individual skill sets.
A VP of cybersecurity in the entertainment industry said: “We’ve been able to focus our standard training on the core Palo Alto Networks capabilities. So, once finished, our team can use their leftover time to take a certificate training. That’s something that can actually grow their career rather than [making them] simply tread water trying to keep up with 10 different solutions.”
-
Increased employee retention.
A CISO in the retail industry explained: “We wanted to figure out how this technology could be used as a retention tool. Can I attract great talent by telling them we have Palo Alto Networks technology and allowing them to build their skill set and increase marketability? Absolutely. Without a doubt. I’ve actually confirmed that in one-on-ones with junior and senior resources on my team. Going with Palo Alto Networks has also bought me some credibility points with my own management. So, on top of helping attract and retain talent, it’s actually made me look good, too.”
Costs. Risk-adjusted PV costs include:
-
Installation and deployment costs totaling $3.4 million over three years.
Time and labor are required to deploy and install all the various components of the Palo Alto Networks solution (including physical and virtual NGFWs) and to bring Prisma SD-WAN to 350 sites.
-
Training costs totaling $156,000 over three years.
Palo Alto Networks required less training than the legacy solutions, and interviewees and respondents reported that the provided trainings were more effective and efficient, allowing employees to get up to speed faster and expand their skill sets.
-
Palo Alto Networks hardware, licensing, and Cloud-Delivered Security Services costs totaling $6.7 million over three years.
The organizations were able to purchase hardware up front and leverage three-year contract terms to add the Cloud-Delivered Security Services, helping reduce the overall costs of NGFW, IPS/IDS, SWG, web proxy, VPN, URL Filtering, malware analysis (e.g., sandboxing), and DNS, SaaS application, and IoT Security solutions. Additionally, deploying services like Prisma Access allows the Cloud-Delivered Security Services to be extended for branch offices or remote workers, and organizations can scale up and down based on usage and needs.
-
SD-WAN deployment costs totaling $1.2 million over three years.
The organizations used a phased deployment strategy for their SD-WAN upgrades, leveraging end-of-life cycles to replace in-store hardware. Negotiating WAN connectivity costs for all sites with the same provider also gave the organizations leverage to further reduce the monthly operating costs at each site.
The financial analysis based on the customer interviews and survey found that a composite organization experiences benefits of $40.1 million over three years versus costs of $11.5 million. This adds up to a net present value (NPV) of $28.5 million and an ROI of 247% that sees payback within six months of purchase.
TEI Framework And Methodology
From the information provided in the interviews and survey, Forrester constructed a Total Economic Impact™ framework for those organizations considering an investment in the Palo Alto Networks network security and SD-WAN solution.
The objective of the framework is to identify the cost, benefit, flexibility, and risk factors that affect the investment decision. Forrester took a multistep approach to evaluate the impact that Palo Alto Networks can have on an organization.
-
DUE DILIGENCE
Interviewed Palo Alto Networks stakeholders and Forrester analysts to gather data.
-
CUSTOMER INTERVIEWS AND SURVEY
Interviewed nine decision-makers and surveyed 133 decision-makers at organizations using Palo Alto Networks to obtain data with respect to costs, benefits, and risks.
-
COMPOSITE ORGANIZATION
Designed a composite organization based on characteristics of the interviewed and surveyed organizations.
-
FINANCIAL MODEL FRAMEWORK
Constructed a financial model representative of the interviews and survey using the TEI methodology and risk-adjusted the financial model based on issues and concerns of the interviewed organizations.
-
CASE STUDY
Employed four fundamental elements of TEI in modeling the investment impact: benefits, costs, flexibility, and risks. Given the increasing sophistication of ROI analyses related to IT investments, Forrester’s TEI methodology provides a complete picture of the total economic impact of purchase decisions. Please see Appendix A for additional information on the New Tech TEI methodology.
DISCLOSURES
Readers should be aware of the following:
This study is commissioned by Palo Alto Networks and delivered by Forrester Consulting. It is not meant to be used as a competitive analysis.
Forrester makes no assumptions as to the potential ROI that other organizations will receive. Forrester strongly advises that readers use their own estimates within the framework provided in the report to determine the appropriateness of an investment in the NGFW.
Palo Alto Networks reviewed and provided feedback to Forrester, but Forrester maintains editorial control over the study and its findings and does not accept changes to the study that contradict Forrester’s findings or obscure the meaning of the study.
Palo Alto Networks provided the customer names for the interviews but did not participate in the interviews.
Forrester fielded the double-blind survey using a third-party survey partner.