Security leaders must deploy strong multifactor security solutions to protect their organizations, users, and customers. Forrester interviewed security leaders from five enterprises using YubiKeys and found that YubiKeys slashed exposure to security breaches from phishing and credential thefts by 99.9% while driving business growth through improved reputation and access to high-security contracts. Further, YubiKeys reduced administrative overhead while providing a flexible, dependable user experience.
YubiKeys are hardware-based, phishing-resistant multifactor authentication (MFA) solutions based on open standards that are produced by Yubico. YubiKeys support a vast range of authentication protocols and come in a wide variety of form factors and connectors, such as USB-A, USB-C, Lightning, and NFC, ensuring that they can be used by almost any organization and user on almost any device.
Yubico commissioned Forrester Consulting to conduct a Total Economic Impact™ (TEI) study and examine the potential return on investment (ROI) enterprises may realize by deploying YubiKeys.1 The purpose of this study is to provide readers with a framework to evaluate the potential financial impact of YubiKeys on their organizations.
To better understand the benefits, costs, and risks associated with this investment, Forrester interviewed five security leaders from organizations that use YubiKeys across their user bases. For the purposes of this study, Forrester aggregated the interviewees’ experiences and combined the results into a single composite organization that is a global company based in North America with 5,000 users and revenue of $2.5 billion per year.
Prior to using YubiKeys, interviewees’ organizations — particularly those not yet using any form of MFA — faced excess and unacceptable exposure to security risks. Security teams expended excess effort on setting and managing password policies while users struggled with frustrating, time-consuming password updates and resets. Organizations with legacy MFA solutions also struggled with poor user experiences, outdated code, lock-in to proprietary technology, and expensive, low-quality hardware.
Interviewees’ organizations adopted modern, phishing-resistant MFA security by deploying YubiKeys and simplified password policies across their systems on the ultimate journey to becoming passwordless. YubiKeys virtually eliminated risk of phishing and credential theft, drove business growth due to improved security levels and reputation, and improved productivity and user experience across the organizations.
Benjamin Brown
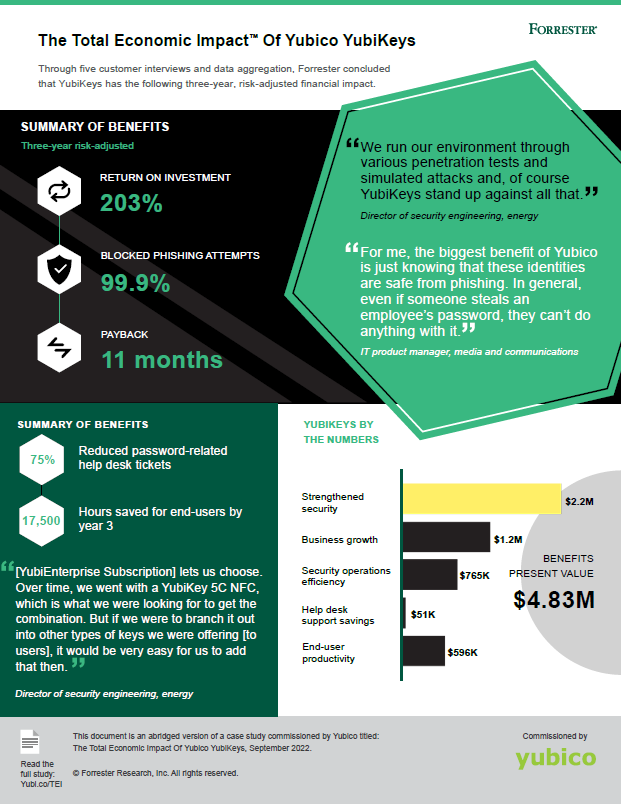
Quantified benefits. Three-year, risk-adjusted present value (PV) quantified benefits for the composite organization include:
-
Strengthened security and reduced risk exposure of $2.2 million.
By deploying YubiKeys across its user base, the composite reduces the risk of successful phishing and credential theft attacks by 99.9%.
-
Improved reputation and ability to win security-related contracts and projects, driving business growth of $1.2 million.
The improved security reputation from using YubiKeys drives a higher deal conversion rate. Additionally, YubiKeys meet the strict security requirements to bid on new opportunities, resulting in more won deals.
-
Security operations efficiency labor savings worth $765,000.
The composite reallocates three FTEs by using YubiKeys to eliminate work related to phishing and credential theft investigation and password management.
-
Help desk support savings of $51,000.
Simplifying password policies with YubiKeys reduces help desk tickets by up to 75%.
-
Improved end user productivity worth $596,000.
End users save 30 minutes per avoided password update and 2 hours per password reset. After adjustments, the organization recaptures almost $57 in annual labor per user by Year 3.
-
Cost savings from decommissioned authentication solutions worth $0 for the composite organization, but which may apply for other organizations.
Organizations that eliminate legacy MFA solutions can save costs and labor by decommissioning the legacy solutions.
Unquantified benefits. Benefits that are not quantified in this study include:
-
Improved security and data protection for end customers and partners.
YubiKeys benefit both direct users and other parties including customers, clients, and partners.
-
Strong and trusted partnership with Yubico.
Security leaders see Yubico as a trusted brand with dependable hardware and great support.
-
Improved employee experience.
Users find YubiKeys easy to use with convenient form factors and connection options, reducing password and hardware frustration.
-
Extensive partner and vendor ecosystem.
Services from Yubico and its partners help customers be successful in their MFA journeys.
Costs. Three-year, risk-adjusted PV costs for the composite organization include:
-
YubiEnterprise Subscription costs of $361,000, based on 5,000 users.
The composite enjoys predictable costs, consistent supplies, replacements, and technical support. YubiEnterprise Subscription begins at 500 users.
-
YubiEnterprise Delivery costs of $52,000.
The composite distributes YubiKeys to its users globally using Yubico’s turnkey delivery program.
-
Deployment costs of $494,000.
The composite deploys YubiKeys during a one-year period with the work of security engineers, IT staff members, cross-functional leaders, and pilot testers.
-
Ongoing management costs of $165,000.
After deploying YubiKeys, the composite requires ongoing management for updates, maintenance, support, training, distribution, and more.
-
End-user training and setup costs of $522,000.
End users typically require up two hours of training, setup, and familiarization when getting a YubiKey and learning to use MFA.
Synopsis. The composite organization invests $1.6 million in costs and experiences $4.8 million in benefits over three years, adding up to a net present value (NPV) of $3.2 million and an ROI of 203%.
Benefits (Three-Year)
Strengthened security Business growth Security operations efficiency Help desk support savings End-user productivity Cost savings from decommisioned authentication solutionsTEI Framework And Methodology
From the information provided in the interviews, Forrester constructed a Total Economic Impact™ framework for those organizations considering an investment in YubiKeys.
The objective of the framework is to identify the cost, benefit, flexibility, and risk factors that affect the investment decision. Forrester took a multistep approach to evaluate the impact that YubiKeys can have on an organization.
Forrester Consulting conducted an online survey of 351 cybersecurity leaders at global enterprises in the US, the UK, Canada, Germany, and Australia. Survey participants included managers, directors, VPs, and C-level executives who are responsible for cybersecurity decision-making, operations, and reporting. Questions provided to the participants sought to evaluate leaders' cybersecurity strategies and any breaches that have occurred within their organizations. Respondents opted into the survey via a third-party research panel, which fielded the survey on behalf of Forrester in November 2020.
-
DUE DILIGENCE
Interviewed Yubico stakeholders and Forrester analysts to gather data relative to YubiKeys.
-
Interviews and survey
Interviewed five representatives at organizations using YubiKeys to obtain data with respect to costs, benefits, and risks.
-
COMPOSITE ORGANIZATION
Designed a composite organization based on characteristics of the interviewees’ organizations.
-
FINANCIAL MODEL FRAMEWORK
Constructed a financial model representative of the interviews using the TEI methodology and risk-adjusted the financial model based on issues and concerns of the interviewees.
-
CASE STUDY
Employed four fundamental elements of TEI in modeling the investment impact: benefits, costs, flexibility, and risks. Given the increasing sophistication of ROI analyses related to IT investments, Forrester’s TEI methodology provides a complete picture of the total economic impact of purchase decisions. Please see Appendix A for additional information on the TEI methodology.
DISCLOSURES
Readers should be aware of the following:
This study is commissioned by Yubico and delivered by Forrester Consulting. It is not meant to be used as a competitive analysis.
Forrester makes no assumptions as to the potential ROI that other organizations will receive. Forrester strongly advises that readers use their own estimates within the framework provided in the study to determine the appropriateness of an investment in YubiKeys.
Yubico reviewed and provided feedback to Forrester, but Forrester maintains editorial control over the study and its findings and does not accept changes to the study that contradict Forrester’s findings or obscure the meaning of the study.
Yubico provided the customer names for the interviews but did not participate in the interviews.